Crypto algorithms
The following algorithms are the pillars of Clipperz password manager and are included in the Javascript Crypto Library.
- SRP - Secure Remote Password
- AES - Advanced Encryption Standard
- SHA2 - Secure Hash Algorithms
- Fortuna PRNG
SRP - Secure Remote Password ↑
SRP provides a better way to perform password-based authentications. It is believed that SRP achieves the theoretical limit of security that can be offered by a purely password-based protocol. In addition, SRP exchanges a cryptographically-strong secret as a byproduct of successful authentication, which enables the two parties to communicate securely.
SRP offers a number of new benefits for password system implementors:
-
An attacker with neither the user’s password nor the host’s password file cannot mount a dictionary attack on the password.
-
An attacker who captures the host’s password file cannot directly compromise user-to-host authentication and gain access to the host without an expensive dictionary search.
-
An attacker who compromises the host does not obtain the the password from a legitimate authentication attempt.
-
An attacker who captures the session key cannot use it to mount a dictionary attack on the password.
Further information is available from the Stanford SRP Authentication Project website and the Wikipedia page.
Clipperz implementation notes
generator g: 2
large prime number n: 115b8b692e0e045692cf280b436735c77a5a9e8a9e7ed56c965f87db5b2a2ece3
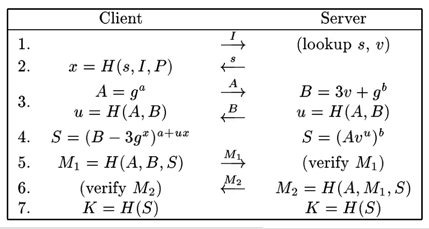
The seven steps of SRP, from SRP-6: Improvements and Refinements to the Secure Remote Password Protocol by Thomas Wu.
AES - Advanced Encryption Standard ↑
The Advanced Encryption Standard (AES) is a block cipher adopted as an encryption standard by the US government. AES was announced by NIST in 2011 after a 5-year standardization process. It became effective as a standard on May 26, 2002.
AES is fast in both software and hardware, is relatively easy to implement, and requires little memory. Currently AES is one of the most popular algorithms used in symmetric key cryptography. AES has a fixed block size of 128 bits and a key size of 128, 192 or 256 bits.
Clipperz implementation notes
cipher mode: CTR
key size: 256 bits
rounds: 14
Click the picture above to enjoy a funny and informative stick figure guide to AES!
SHA2 - Secure Hash Algorithms ↑
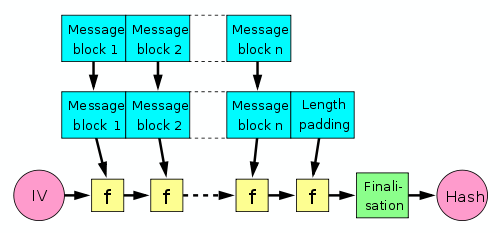
SHA2 refers to a family of cryptographic hash functions developed by NSA and standardized by NIST. Hash functions can process a message to produce a condensed representation called a message digest.
These algorithms enable integrity checks: any change to the message will result in a different message digest. This property is useful in the generation and verification of digital signatures and message authentication codes, and in the generation of random numbers. Learn more on Wikipedia.
Clipperz implementation notes
In order obtain the 128-bit security level and eliminate some weaknesses due to the iterative nature of the SHA2 family, the hash function used throughout Clipperz has a 256-bit output and is defined as follows:
Double-SHA-256(m) = SHA-256(SHA-256(m))
IV: random
Fortuna PRNG ↑
High quality random bits are crucial to strong crypto systems. Fortuna is a novel but well analyzed pseudo-random number generator (PRNG) devised by Bruce Schneier and Niels Ferguson while writing the book Practical Cryptography. Fortuna is based on an entropy accumulator which collects genuinely random data from various sources and uses them to reseed the generator when enough new randomness has arrived. Therefore Fortuna leaves to implementors the choice of the entropy sources to be used.
Unless an attacker is able to control all the sources of alleged entropy flowing into the system, it will remain secure.
Clipperz implementation notes
Block cipher used by the generator: AES-256 in CTR mode
Entropy sources:
- mouse movements
- internal clock
- keyboard activity
- built-in crypto.getRandomValues() of modern browsers

 Mastodon
Mastodon GitHub
GitHub Twitter
Twitter Google
forum
Google
forum